DMZ Gateway
Version 24.3.9159
Version 24.3.9159
DMZ Gateway
CData Arc can receive secure connections through a demilitarized zone (DMZ) gateway. Using a DMZ protects corporate firewalls and maintains network security by funneling all external connection attempts to the DMZ.
Note: This feature is currently only available if you use the embedded web server included with the .NET edition of Arc.
How the Gateway Works
Arc supports establishing an SSH reverse tunnel to receive data sent to the DMZ. Here’s how it works:
- An SSH server sits in the DMZ and transfers data between Arc and external trading partners.
- Arc connects to this SSH server and opens an SSH reverse tunnel on any open port (for example, port 7777).
- Once the tunnel has been opened, the SSH server forwards any traffic it receives on port 7777 directly to Arc.
- Trading partners connect to the SSH server and send any data intended for Arc to port 7777.
- The data is forwarded from the SSH server to Arc using the SSH standard for transport security.
This configuration allows trading partners to send business data to Arc while only having access to the SSH server in the DMZ.
Setting Up the Gateway
Follow these steps to enable DMZ gateway support:
-
Install an SSH server in the DMZ or choose a DMZ with an SSH server already installed—for example, an Amazon Machine Image (AMI) pre-loaded with an SSH server, or a free OpenSSH server implementation installed on a DMZ machine.
-
Enable port forwarding in the SSH server. To do this, open the server’s
sshd_configfile and setGatewayPortsto yes. -
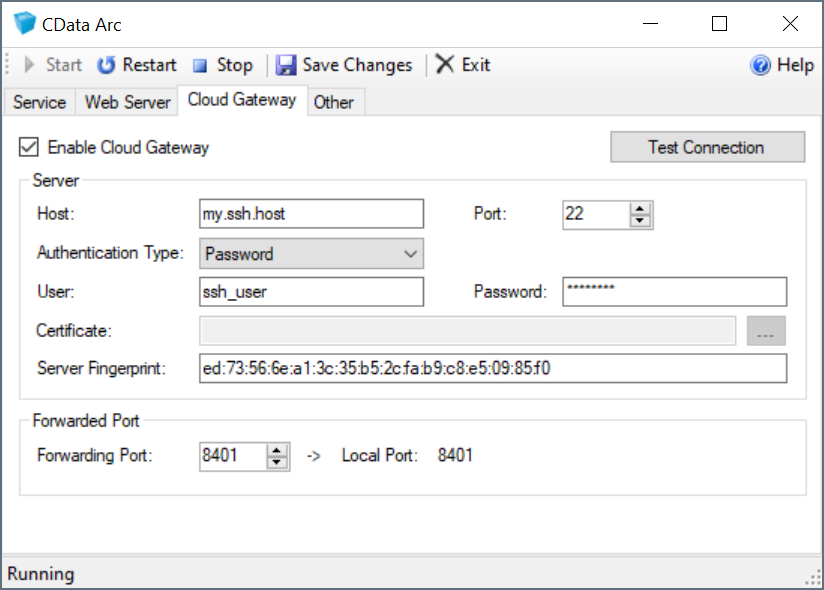
Right-click the Arc icon in the system tray, select Server Options, and navigate to the Cloud Gateway tab.
-
Check Enable Cloud Gateway.
-
In the Server section, configure the connection settings for the SSH server in the DMZ.
-
In the Forwarded Port section, set the Forwarding Port to the port on the SSH server to use when forwarding data to Arc. You can also forward two additional ports to establish tunnels for SFTP and OFTP ports. See Additional Forwarding Ports for details.
-
Click Test Connection button to verify that the connection is successful.
-
Restart the Arc embedded web sever to automatically open an SSH reverse tunnel on the specified port.
After the above steps are complete, provide trading partners with connection details to the SSH server in the DMZ. Instruct them to send data to this SSH server on the port specified by Forwarding Port instead of the default port (22).
Additional Forwarding Ports
Configuring the Forwarding Port allows traffic to be forwarded for the HTTP traffic used in Arc. You can also forward two other ports to establish tunnels for SFTP and OFTP ports.
To forward additional ports, add the following four lines to the arc.xml configuration file in the installation directory webapp folder:
<OFTPPort>6619</OFTPPort>
<OFTPRemotePort>6619</OFTPRemotePort>
<SFTPPort>22</SFTPPort>
<SFTPRemotePort>2022</SFTPRemotePort>
<type>Port is the port that the traffic is forwarded to and <type>RemotePort is the port to open on the SSH server.
Note: You cannot forward the port that is already being used for the SSH service. For example, if the SSH server is listening on port 22, the SFTPRemotePort cannot also be port 22.
Maintaining the Gateway
Arc automatically opens the gateway when the server (re)starts. Arc also handles reconnecting to the SSH server if the connection is dropped for any reason. No user maintenance is required to keep the gateway up and running.