Installing and Configuring DBAmp
Installing and Configuring DBAmp
Installing the CData DBAmp Windows Service
Run the CData DBAmp setup application to install the CData DBAmp Windows Service:
Creating the DBAmp Linked Server
-
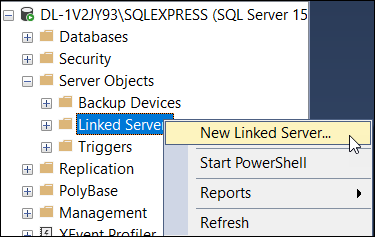
In MS SQL Server Management Studio, create a new linked server by going to the Server Objects > Linked Servers tree in the Object Explorer. Right-Click Linked Servers > New Linked Server:
-
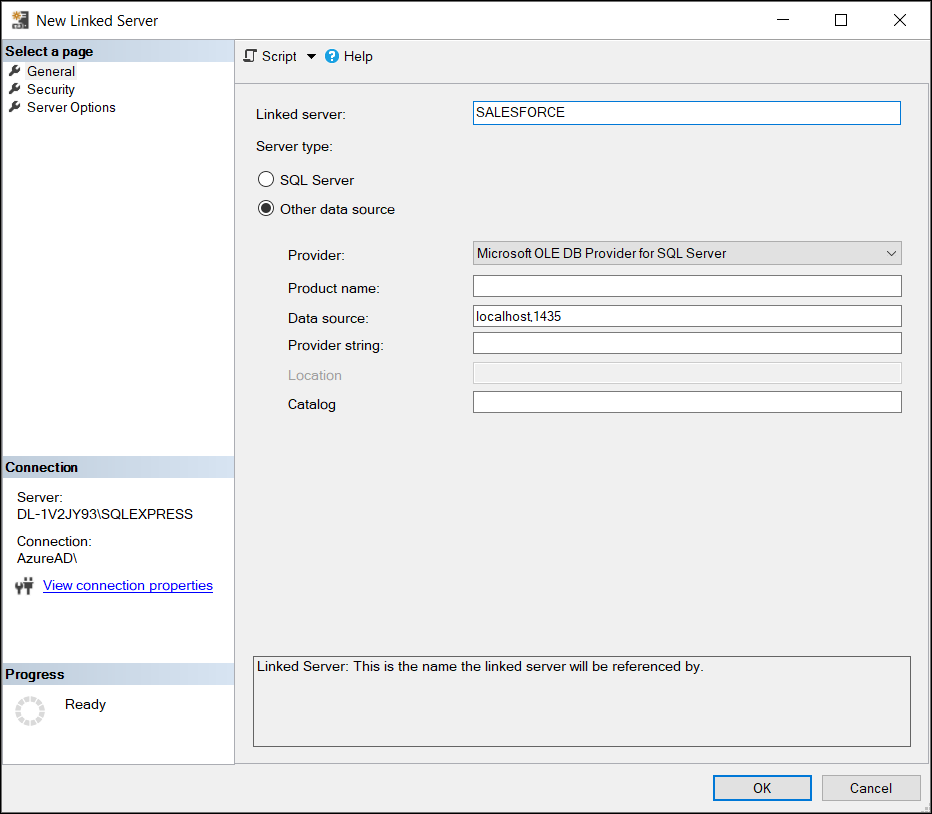
Enter the following information on the General page of the Linked Server:
-
Linked Server—the name of your DBAmp linked server.
-
Provider—choose Microsoft OLE DB Driver for SQL Server or Microsoft OLE DB Provider for SQL Server. Typically, both are acceptable but your environment may only support one.
-
Date Source—localhost,1435
-
Provider String—if you are connecting to a sandbox, enter App=https://test.salesforce.com. Otherwise, leave blank. * Additional caveats—if you are connecting to a sandbox or are part of an organization that requires MyDomain URL logins, and you are using a non-admin or non-Windows account, then the Provider string must also include the UserId parameter, for example: App= your URL;User ID=your username. If you do not use a Provider string, the account type you choose is irrelevant.
-
-
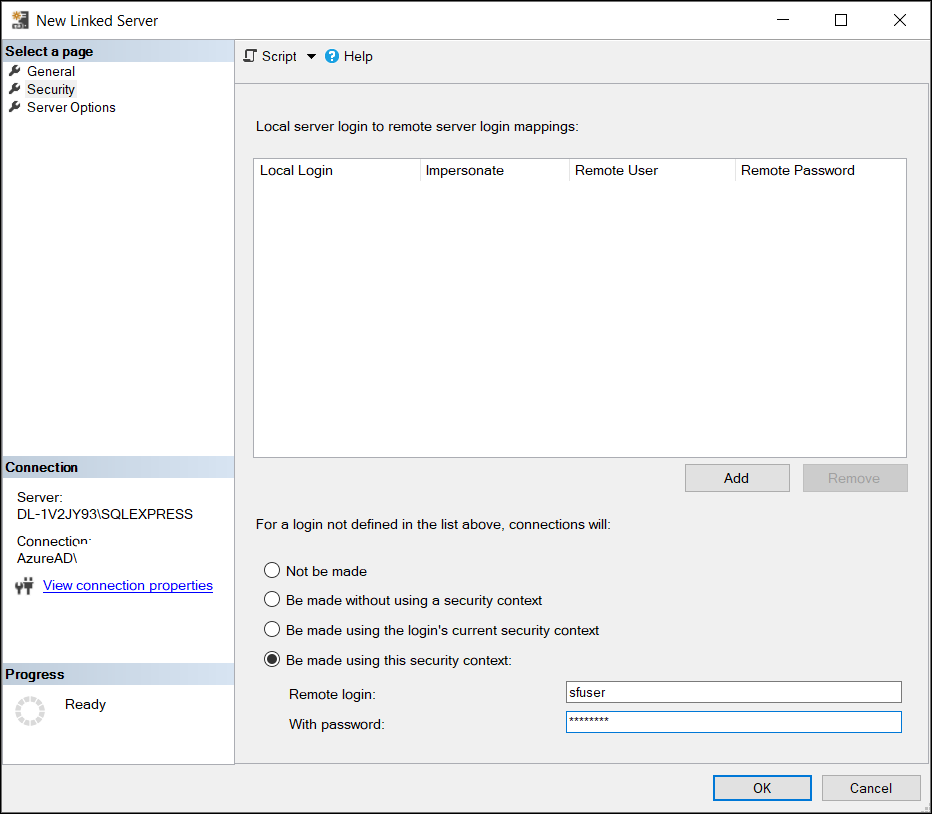
Select Be made using this security context on the Security page of the Linked Server and enter your Salesforce credentials:
-
Remote Login—Salesforce username
-
With Password—your Salesforce password with your Security Token appended
-
-
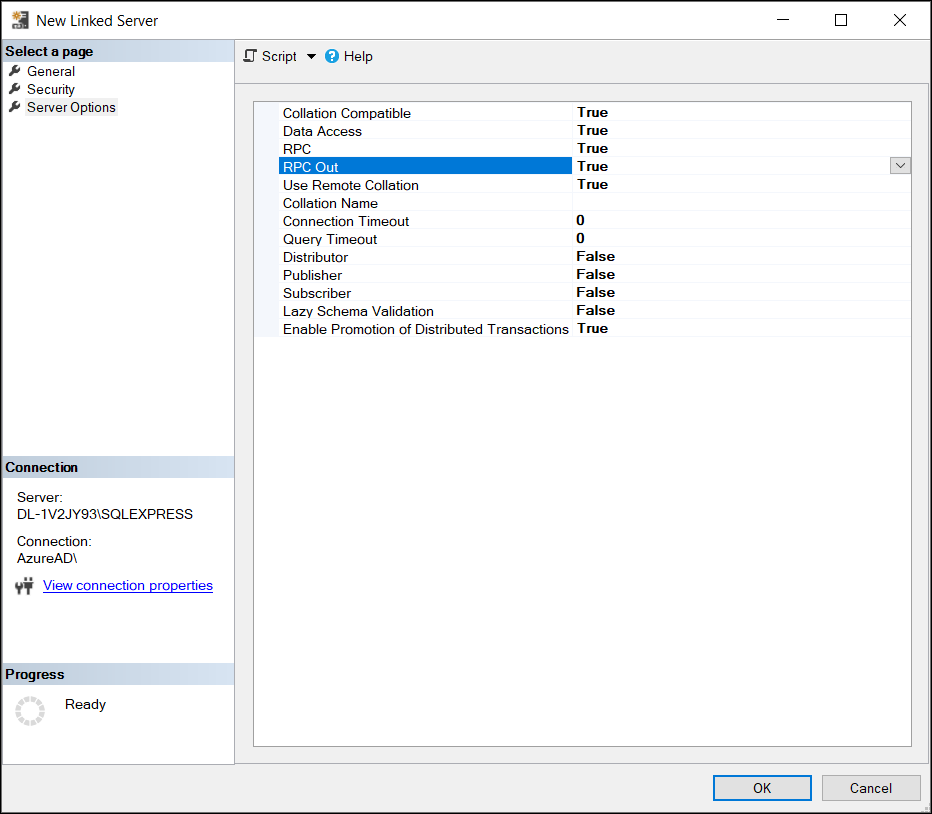
Check the following options are true on the Server Options page of the Linked Server:
-
Collation Compatible
-
Data Access
-
RPC
-
RPC Out
-
Use Remote Collation
-
-
Click OK to create the DBAmp Linked Server.
Installing DBAmp Stored Procedures
Next, either create a database to run DBAmp commands, or install the stored procedures in each existing data base that you want to use. After installation, your databases contain the DBAmp stored procedures and the local replicated tables you make from your live Salesforce.com data.
NOTE: If you did not install DBAmp in the default directory, the .sql file is located somewhere else. In this case, you must edit the Create DBAmp SPROCS.sql script to find all instances of bin folders:
set @ProgDir = 'C:\"Program Files"\CData\"CData DBAmp"\bin\'
Then edit the file path to reflect the bin folder of whatever directory you installed it in.
To install the DBAmp Stored Procedures:
-
Either create a new database, or select existing databases in which you want to include stored procedure support. In either case, you must install stored procedures in the selected databases. These databases hold all the local replicated tables and the DBAmp stored procedures.
-
Open the file
Create DBAmp SPROCS.sqlin the Query Analyzer or in Management Studio but do not execute it yet. The file is located in\ProgramFiles\CData\CData DBAmp\SQL. -
Make sure that default database shown on the toolbar is the Salesforce backups database (not the main database). Then press F5 to add the stored procedures to the database.
Specifying DBAmp Configuration Program Settings
When you ran the CDA DBAmp setup application, along with the Windows service it installed the DBAmp Configuration Program. If you had a previous version of DBAmp installed on your server, there is an option in the new DBAmp Configuration Program to migrate the settings in the old DBAmp Configuration program. To do so, run the new DBAmp Configuration Program and select Configuration > Migrate Old Settings.
If you are a new user, follow these steps to set up the DBAmp Configuration program.
-
Run the DBAmp Configuration program, located at
C:\Program Files\CData\CData DBAmp\bin\DBAmp Config2. -
Select Configuration > Settings in the menu bar:
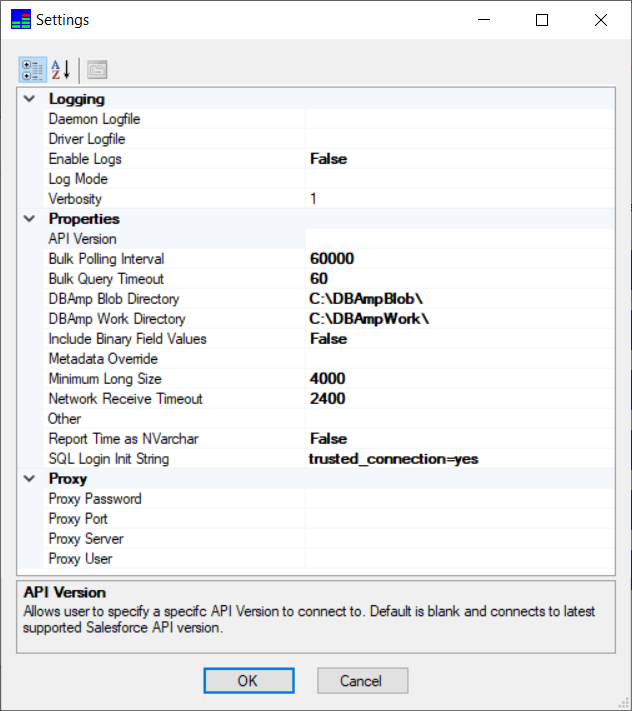
This opens the Settings page:
-
Use this page to configure:
NOTE: When specifying directories, keep in mind that large downloads can greatly expand directory size. Make sure you have enough disk space allocated.
Enabling xp_cmdshell for DBAmp
The DBAmp stored procedure uses the xp_cmdshell command. If you are not an SQL Server administrator, you must have the proper permission to use this command. See the SQL Server xp_cmdshell documentation for more information.
Pointing DBAmp to Your Salesforce Sandbox instance
By default, DBAmp points to your production Salesforce.com instance. If you need to change DBAmp to point to your sandbox instance or to a different endpoint for DBAmp, alter the Provider String parameter of your linked server.
Provider String is normally blank. If the linked server needs to connect to a sandbox instance, then enter App=https://test.Salesforce.com for the Provider String Parameter on the linked server General page.
Advanced Configuration Settings for SSLcd
SSL is always enabled because it is required by SQL Server, but if you have special requirements, you can set the exact ciphers and protocols you want to use by editing the Microsoft Windows registry.
To improve TLS/SSL security, set SSLProtocols and SSLCipherSuites. SSLProtocols specifies which version of TLS you want to use. SSLCipherSuites specifies the encryption you want to use.
You can set both values in Computer\HKEY_LOCAL_MACHINE\SOFTWARE\CData\CData SQL Broker\Config. For SSLProtocols, use the DWORD value type and set one or more of the following:
- 192: TLS1
- 768: TLS1_1
- 3072: TLS1_2
- 12288: TLS1_3
To combine protocols, add their values. For example, to specify TLS1_1 and TSL1_2, add 768+3072 and set the value to 3840.
</ul>
For SSLCipherSuites in the same registry entry, set the string value to one of the following:
- TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384
- TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256
- TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
- TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
- TLS_ECDH_ECDSA_WITH_AES_256_GCM_SHA384
- TLS_RSA_WITH_AES_256_GCM_SHA384
- TLS_RSA_WITH_AES_128_GCM_SHA256
- TLS_ECDH_ECDSA_WITH_AES_128_GCM_SHA256
- TLS_DHE_DSS_WITH_AES_256_GCM_SHA384
- TLS_DHE_RSA_WITH_AES_256_GCM_SHA384
- TLS_ECDH_RSA_WITH_AES_256_GCM_SHA384
- TLS_ECDH_RSA_WITH_AES_128_GCM_SHA256
- TLS_DHE_RSA_WITH_AES_128_GCM_SHA256
- TLS_DHE_DSS_WITH_AES_128_GCM_SHA256
- TLS_DH_RSA_WITH_AES_128_GCM_SHA256 (Not Recommended)
- TLS_DH_RSA_WITH_AES_256_GCM_SHA384 (Not Recommended)
- TLS_DH_DSS_WITH_AES_128_GCM_SHA256 (Not Recommended)
- TLS_DH_DSS_WITH_AES_256_GCM_SHA384 (Not Recommended)
- TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384
- TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256
- TLS_ECDH_ECDSA_WITH_AES_256_CBC_SHA384
- TLS_DHE_DSS_WITH_AES_256_CBC_SHA256
- TLS_RSA_WITH_AES_256_CBC_SHA256
- TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384
- TLS_ECDH_RSA_WITH_AES_256_CBC_SHA384
- TLS_DHE_RSA_WITH_AES_256_CBC_SHA256
- TLS_DHE_RSA_WITH_AES_128_CBC_SHA256
- TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256
- TLS_RSA_WITH_AES_128_CBC_SHA256
- TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA256
- TLS_ECDH_RSA_WITH_AES_128_CBC_SHA256
- TLS_DHE_DSS_WITH_AES_128_CBC_SHA256
- TLS_RSA_WITH_AES_256_CBC_SHA
- TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA
- TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA
- TLS_ECDH_ECDSA_WITH_AES_256_CBC_SHA
- TLS_DHE_RSA_WITH_AES_256_CBC_SHA
- TLS_ECDH_RSA_WITH_AES_256_CBC_SHA
- TLS_DHE_DSS_WITH_AES_256_CBC_SHA
- TLS_RSA_WITH_AES_128_CBC_SHA
- TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA
- TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA
- TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA
- TLS_ECDH_RSA_WITH_AES_128_CBC_SHA
- TLS_DHE_RSA_WITH_AES_128_CBC_SHA
- TLS_DHE_DSS_WITH_AES_128_CBC_SHA
- TLS_ECDHE_ECDSA_WITH_3DES_EDE_CBC_SHA
- TLS_ECDHE_RSA_WITH_3DES_EDE_CBC_SHA
- TLS_ECDH_ECDSA_WITH_3DES_EDE_CBC_SHA
- TLS_ECDH_RSA_WITH_3DES_EDE_CBC_SHA
- TLS_DHE_RSA_WITH_3DES_EDE_CBC_SHA
- TLS_DHE_DSS_WITH_3DES_EDE_CBC_SHA
- TLS_RSA_WITH_3DES_EDE_CBC_SHA
- TLS_RSA_WITH_DES_CBC_SHA
- TLS_DHE_RSA_WITH_DES_CBC_SHA
- TLS_DHE_DSS_WITH_DES_CBC_SHA
- TLS_RSA_WITH_RC4_128_MD5
- TLS_RSA_WITH_RC4_128_SHA
</ul>
For TLS1_3 only:
- TLS_AES_256_GCM_SHA384
- TLS_CHACHA20_POLY1305_SHA256
- TLS_AES_128_GCM_SHA256 </ul>