TCP Server Connector
Version 23.4.8841
Version 23.4.8841
TCP Server Connector
TCP Server connectors support hosting a generic endpoint for receiving data over TCP.
Overview
Each TCP Server connector listens on a specified port for incoming TCP traffic, either with TLS/SSL encryption or plain text. Use this connector when CData Arc needs to receive arbitrary data that does not necessarily fit into the constraints provided by other standard protocols.
Since TCP traffic is a constant stream that does not intrinsically have a start or end point, you must configure the connector to determine where one message ends and the next begins. The connector supports two approaches:
- A static string/character delimiter that ends the current message or begins the next message
- Reading a value in the incoming TCP data to determine how long the message should be
For the second approach, the connector requires an offset (how many bytes after the first byte to begin reading the message length) and a size (how many bytes to read, starting at the offset, to get the length value). If the length of the message is the first value in the header for the message, the offset is 0.
Once the delimiter or length is reached, the connector pushes a message into the Arc flow containing the raw data received over TCP.
The TCP Server connector can also generate an Arc message when a client connects or disconnects, to alert other processes within the flow. See the Connected and Disconnected Messages section for more information.
For information on sending responses back to TCP clients, see the Sending Messages section.
Connector Settings
Settings Tab
Configuration
Settings related to the core configuration of the connector.
- Connector Id The static, unique identifier for the connector.
- Connector Type Displays the connector name and a description of what it does.
- Connector Description An optional field to provide a free-form description of the connector and its role in the flow.
- Port The port on which to listen for incoming TCP connections.
Message Decoding
Settings related to distinguishing individual messages from the TCP stream.
- Message Start Delimiter The character or string indicating the start of a new message.
- Message End Delimiter The character or string indicating the end of the current message.
- Message Length Offset The number of bytes to skip before beginning to read the length of the message from the incoming data.
- Message Length Size The size in bytes of the length value in the incoming data.
TLS Settings
Settings related to TLS/SSL transport security.
- Enable TLS Whether clients must negotiate TLS/SSL encryption to connect to the TCP server.
- Server Certificate The TLS/SSL certificate that identifies the TCP server.
- Certificate Password The password to access the server certificate’s private key.
Automation Tab
Automation
Settings related to the automatic processing of files by the connector.
- Send Whether messages arriving at the connector are automatically processed.
Performance
Settings related to the allocation of resources to the connector.
- Max Workers The maximum number of worker threads consumed from the threadpool to process files on this connector. If set, this overrides the default setting on the Settings > Automation page.
- Max Files The maximum number of files sent by each thread assigned to the connector. If set, this overrides the default setting on the Settings > Automation page.
アラートタブ
アラートとサービスレベル(SLA)の設定に関連する設定.
コネクタのE メール設定
サービスレベル(SLA)を実行する前に、通知用のE メールアラートを設定する必要があります。アラートを設定をクリックすると、新しいブラウザウィンドウで設定ページが開き、システム全体のアラートを設定することができます。詳しくは、アラートを参照してください。
サービスレベル(SLA)の設定
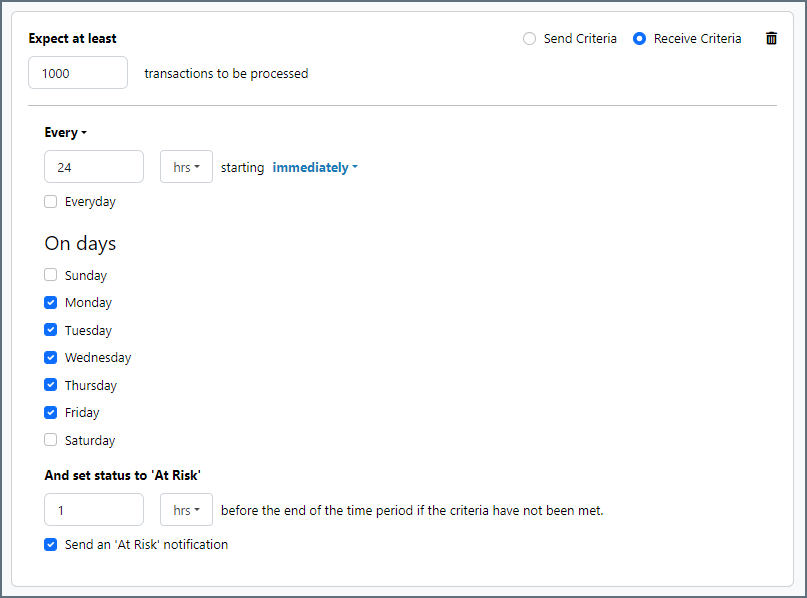
サービスレベルでは、フロー内のコネクタが送受信すると予想される処理量を設定し、その量が満たされると予想される時間枠を設定できます。CData Arc は、サービスレベルが満たされていない場合にユーザーに警告するE メールを送信し、SLA を At Risk(危険) としてマークします。これは、サービスレベルがすぐに満たされない場合に Violated(違反) としてマークされることを意味します。これにより、ユーザーはサービスレベルが満たされていない理由を特定し、適切な措置を講じることができます。At Risk の期間内にサービスレベルが満たされなかった場合、SLA はViolated としてマークされ、ユーザーに再度通知されます。
サービスレベルを定義するには、予想処理量の条件を追加をクリックします。
- コネクタに個別の送信アクションと受信アクションがある場合は、ラジオボタンを使用してSLA に関連する方向を指定します。
- 検知基準(最小)を、処理が予想されるトランザクションの最小値(量)に設定し、毎フィールドを使用して期間を指定します。
- デフォルトでは、SLA は毎日有効です。これを変更するには、毎日のチェックをOFF にし、希望する曜日のチェックをON にします。
- 期間終了前にステータスを’At Risk’ に設定するタイミングを使用して、SLA がAt Risk としてマークされるようにします。
- デフォルトでは、通知はSLA が違反のステータスになるまで送信されません。これを変更するには、‘At Risk’ 通知を送信のチェックをON にします。
次の例は、月曜日から金曜日まで毎日1000ファイルを受信すると予想されるコネクタに対して構成されたSLA を示しています。1000ファイルが受信されていない場合、期間終了の1時間前にAt Risk 通知が送信されます。
Advanced Tab
Keep Alive
Settings related to keep-alive packets sent by the server to maintain an idle connection.
- Keep Alive Whether to send keep-alive packets periodically to ensure that idle connections are not closed due to inactivity.
- Keep Alive Time The length of inactivity that should elapse before sending the first keep-alive packet.
- Keep Alive Interval The interval between consecutive keep-alive packets.
Advanced Settings
Settings not included in the previous categories.
- Connected Messages Whether the connector should generate an Arc message when a client connects. See the Connected and Disconnected Messages section for more information.
- Disconnected Messages Whether the connector should generate an Arc message when a client disconnects. See the Connected and Disconnected Messages section for more information.
- Idle Timeout The length of time (in seconds) the server should wait for an idle client before disconnecting them due to inactivity.
- Local File Scheme A scheme for assigning filenames to messages that are output by the connector. You can use macros in your filenames dynamically to include information such as identifiers and timestamps. For more information, see Macros.
- Local Host The binding address of the local server, if not the default network interface.
- Max Connections The maximum number of concurrent connectors.
- TLS Enabled Protocols The list of TLS/SSL protocols supported when establishing outgoing connections. Best practice is to only use TLS protocols. Some obsolete operating systems do not support TLS 1.2.
Message
- Save to Sent Folder Check this to copy files processed by the connector to the Sent folder for the connector.
- Sent Folder Scheme Instructs the connector to group messages in the Sent folder according to the selected interval. For example, the Weekly option instructs the connector to create a new subfolder each week and store all messages for the week in that folder. The blank setting tells the connector to save all messages directly in the Sent folder. For connectors that process many messages, using subfolders helps keep messsages organized and improves performance.
Logging
- Log Level The verbosity of logs generated by the connector. When you request support, set this to Debug.
- Log Subfolder Scheme Instructs the connector to group files in the Logs folder according to the selected interval. For example, the Weekly option instructs the connector to create a new subfolder each week and store all logs for the week in that folder. The blank setting tells the connector to save all logs directly in the Logs folder. For connectors that process many transactions, using subfolders helps keep logs organized and improves performance.
- Log Messages Check this to have the log entry for a processed file include a copy of the file itself. If you disable this, you might not be able to download a copy of the file from the Input or Output tabs.
Miscellaneous
Miscellaneous settings are for specific use cases.
- Other Settings Enables you to configure hidden connector settings in a semicolon-separated list (for example,
setting1=value1;setting2=value2). Normal connector use cases and functionality should not require the use of these settings.
Server Tab
The following functions are available in the Trusted IP Addresses section:
- Add Opens a modal to enter a new IP address range.
- Edit Opens a modal to modify the selected IP address range.
- Delete Deletes the selected IP address range from the list.
The following restrictions apply to this feature:
localhostcannot be modified or removed from the list.- Any IP addresses outside of the defined ranges are rejected.
- Ranges are supported. For example, the entry
100.10.100.1-15indicates that IP addresses between100.10.100.1and100.10.100.15are allowed. - Classless inter-domain routing (CIDR) notation is supported. For example, the entry
100.10.100.0/24indicates that IP addresses between100.10.100.0and100.10.100.255are allowed. - Wildcard patterns are supported. For example, the entry
100.10.100.*indicates that IP addresses beginning with100.10.100are allowed.
Connected and Disconnected Messages
By default, the TCP Server connector only generates Arc messages when clients transfer data that the connector recognizes as a full message (according to the settings in the Message Decoding section). The connector can also generate Arc messages when a client connects to the server (if Connected Messages is enabled on the Advanced tab) or disconnects from the server (if Disconnected Messages is enabled on the Advanced tab).
When these special messages are generated, a special header is added to the Arc message:
x-tcpserver-event
This header is set to the value connected when clients are connecting, and disconnected when clients are disconnecting.
This header value must be checked by later connectors in the flow to detect whether a message written to the output folder of a TCP Server connector is one of these special messages.
Sending Messages
The TCP Server connector also uses a special header value to send messages back to connected clients:
x-tcpserver-connectionid
This header is added to any output messages generated by the connector, and is set to a Connection ID value that uniquely identifies the connected client. Messages that should be sent back to this client must have this header set to the same value to ensure that the message is sent to the appropriate client.
Since this header is already present on any messages written out by the connector, if the message passes through an Arc flow and arrives back at the Input for the TCP Server connector, it still has the same Connection ID value and is returned to the client that sent the original message. If the message cannot be directly routed back to the TCP Server connector, the Connection ID value must be saved and applied as a header (with the name shown above) to any new messages that should be returned to the client.
Macros
Using macros in file naming strategies can enhance organizational efficiency and contextual understanding of data. By incorporating macros into filenames, you can dynamically include relevant information such as identifiers, timestamps, and header information, providing valuable context to each file. This helps ensure that filenames reflect details important to your organization.
CData Arc supports these macros, which all use the following syntax: %Macro%.
| Macro | Description |
|---|---|
| ConnectorID | Evaluates to the ConnectorID of the connector. |
| Ext | Evaluates to the file extension of the file currently being processed by the connector. |
| Filename | Evaluates to the filename (extension included) of the file currently being processed by the connector. |
| FilenameNoExt | Evaluates to the filename (without the extension) of the file currently being processed by the connector. |
| MessageId | Evaluates to the MessageId of the message being output by the connector. |
| RegexFilename:pattern | Applies a RegEx pattern to the filename of the file currently being processed by the connector. |
| Header:headername | Evaluates to the value of a targeted header (headername) on the current message being processed by the connector. |
| LongDate | Evaluates to the current datetime of the system in long-handed format (for example, Wednesday, January 24, 2024). |
| ShortDate | Evaluates to the current datetime of the system in a yyyy-MM-dd format (for example, 2024-01-24). |
| DateFormat:format | Evaluates to the current datetime of the system in the specified format (format). See サンプル日付フォーマット for the available datetime formats |
| Vault:vaultitem | Evaluates to the value of the specified vault item. |
| ConnectionId | Evaluates to the ConnectionId of the connection a client used to upload data. |
| RemoteHost | Evaluates to the ConnectionId of the connection that the client used to upload data. |
Examples
Some macros, such as %Ext% and %ShortDate%, do not require an argument, but others do. All macros that take an argument use the following syntax: %Macro:argument%
Here are some examples of the macros that take an argument:
- %Header:headername%: Where
headernameis the name of a header on a message. - %Header:mycustomheader% resolves to the value of the
mycustomheaderheader set on the input message. - %Header:ponum% resolves to the value of the
ponumheader set on the input message. - %RegexFilename:pattern%: Where
patternis a regex pattern. For example,%RegexFilename:^([\w][A-Za-z]+)%matches and resolves to the first word in the filename and is case insensitive (test_file.xmlresolves totest). - %Vault:vaultitem%: Where
vaultitemis the name of an item in the vault. For example,%Vault:companyname%resolves to the value of thecompanynameitem stored in the vault. - %DateFormat:format%: Where
formatis an accepted date format (see サンプル日付フォーマット for details). For example,%DateFormat:yyyy-MM-dd-HH-mm-ss-fff%resolves to the date and timestamp on the file.
You can also create more sophisticated macros, as shown in the following examples:
- Combining multiple macros in one filename:
%DateFormat:yyyy-MM-dd-HH-mm-ss-fff%%EXT% - Including text outside of the macro:
MyFile_%DateFormat:yyyy-MM-dd-HH-mm-ss-fff% - Including text within the macro:
%DateFormat:'DateProcessed-'yyyy-MM-dd_'TimeProcessed-'HH-mm-ss%