OFTP Connector
Version 24.2.9039
Version 24.2.9039
OFTP Connector
The OFTP connector sends and receives files via the Odette FTP protocol.
Overview
An OFTP connection is configured in two places. Configure the OFTP Profiles page with an Odette identifier, settings for the local OFTP server, and other information that is global across all OFTP connections. Then configure individual OFTP connectors with connection settings specific to a single trading partner (a single OFTP entity).
For information on routing an OFTP message through a separate OFTP entity (for example, a clearinghouse), see Message Routing.
Profile Configuration
The OFTP profile must be configured before connections can be established with individual OFTP connectors. Click Profiles > OFTP on the top menu bar.
OFTP Profile Tab
Personal Id
Settings for identifying the local profile.
- Odette Identifier (SSID Code) Your Odette identifier. This value is included in outgoing transmissions to identify the sender, and incoming messages must be addressed to this identifier. Odette identifiers are provided by the Odette organization.
- Password (SSID Password) The password associated with the Odette Identifier. You can choose this value as long as your trading partners have the same value configured on their systems.
Server Settings
Settings related to the OFTP server implementation.
- Port The port on which the server listens for incoming connections.
- SSL/TLS Whether SSL/TLS must be negotiated to connect to the server.
- TLS Private Certificate If TLS/SSL is enabled, specify the TLS/SSL certificate required to verify the server’s identify.
- Certificate Password The password required to access the TLS/SSL certificate.
Personal Certificate
Settings related to the private decryption and signature certificate.
- Data Decryption Certificate The certificate used to decrypt incoming messages and sign outgoing messages. Never share this certificate with external parties. Click the Create Certificate button to generate a self-signed certificate that is ready to use in an OFTP transaction; a corresponding public key certificate is also generated with the same filename and a
.cerextension. - Certificate Password The password required to access the Data Decryption Certificate.
Optional Certificate Settings
Optional settings to define parameters for a certificate.
- Auth Challenge Private Certificate A certificate with a private key used when challenged by the server to verify authenticity. Accepts PKCS#12 certificates in
.pfxor.p12formats. - Certificate Password The private certificate password.
- Sign Private Certificate A certificate with a private key used when signing sent messages. Accepts PKCS#12 certificates in
.pfxor.p12formats. - Certificate Password The private certificate password.
- Strong Certificate Verification Only allow strong certificate verification from trusted certificate authorities.
Advanced Settings
- Inactivity Timeout The length of time (in seconds) to wait before closing inactive connections to the server.
Lockouts
Optional settings related to locking server access.
- Failed Attempts The number of unsuccessful login attempts allowed before the user is locked out.
- Lockout Period The length of time (in minutes) that the user is locked out.
- Time Check Period The length of time (in minutes) that records are kept of failed login attempts.
Trusted IP Addresses
次の機能は、信頼されたIP アドレスセクションで利用可能です。
- 追加 新しいIP アドレスの範囲を入力するためのモーダルを開きます。
- 編集 選択されたIP アドレスの範囲を編集するためのモーダルを開きます。
- 削除 選択されたIP アドレスの範囲をリストから削除します。
この機能には次の制約が適用されます。
localhostを編集したり、リストから削除することはできません。- 定義された範囲外のIP アドレスは拒否されます。
- 範囲指定に対応しています。例えば、エントリ
100.10.100.1-15は、100.10.100.1から100.10.100.15までのIP アドレスが許可されることを示します。 - Classless Inter-Domain Routing (CIDR) 表記に対応しています。例えば、エントリ
100.10.100.0/24は、100.10.100.0から100.10.100.255までのIP アドレスが許可されることを示します。 - ワイルドカードのパターンに対応しています。例えば、エントリ
100.10.100.*は、100.10.100で始まるIP アドレスが許可されることを示します。
Logging
Settings that govern the creation and storage of logs.
- Log Level The verbosity of logs generated by the connector. When you request support, set this to Debug.
- Log Rotate Interval The number of days to wait before creating a new log file.
- Log Delete Interval The number of days to wait before deleting old log files.
Miscellaneous
Miscellaneous settings are for specific use cases.
- Other Settings Enables you to configure hidden connector settings in a semicolon-separated list (for example,
setting1=value1;setting2=value2). Normal connector use cases and functionality should not require the use of these settings.
Connector Configuration
This section contains all of the configurable connector properties.
Settings Tab
Host Configuration
Settings related to the remote OFTP entity to connect to.
- コネクタId コネクタの静的な一意の識別子。
- コネクタの種類 コネクタ名とその機能の説明が表示されます。
- コネクタの説明 コネクタとフローにおけるロールについて自由形式の説明を記載するオプションのフィールド。
- Identifier The Odette identifier for the remote OFTP entity (the trading partner’s identifier).
- Password The password associated with the partner’s identifier.
- Version The version of the OFTP protocol to use when exchanging files.
- Remote Host The hostname or IP address of the remote OFTP server.
- Port The port on which to connect to the remote OFTP server.
- Connection Timeout The length of time (in seconds) the connector waits for a connection response before throwing a timeout error.
- Use SSL/TLS Whether to negotiate SSL/TLS when connecting to the remote OFTP server.
- Secure Odette Authentication Whether to perform application-layer encryption and decryption. To perform this authentication, you must specify both a signing and encryption certificate.
Connection Info
Settings related to the OFTP connection parameters.
- Virtual File Format The OFTP file format to use when transmitting files.
- Virtual File Security Whether to sign and/or encrypt outgoing messages.
- Compression Whether to compress outgoing messages.
- Signed Receipts Whether outgoing messages should request or require a signed receipt to be returned.
Trading Partner Certificates
Settings related to the public key certificates provided by the trading partner.
- Encryption Certificate The public key certificate used for encryption when sending messages. This certificate must be paired with the trading partner’s private decryption certificate. The trading partner must provide this public key certificate when sharing their OFTP configuration details.
- TLS Server Certificate TLS / SSL サーバーのID を検証するために使用される公開鍵証明書。ターゲットサーバーがTLS / SSL を使用する場合は、このフィールドにサーバーを識別する証明書を設定します。サーバーの証明書が利用できない場合は、この設定を空白のままにして基盤となるOS / JVM に証明書の検証を実行させるか、
任意の証明書に設定してサーバーのID を暗黙的に信頼させることができます。
Routing
Settings related to routing an OFTP message through a separate OFTP entity.
- Routing Partner If outgoing OFTP messages should be routed through an OFTP entity that is separate from the target OFTP entity, set this field to the OFTP connector that is configured to connect to the intermediary OFTP server.
For example, if the connector needs to send files to serverA and route the file through serverB, configure the connector to connect to serverA and set this field to an OFTP connector configured to connect to serverB. See Message Routing for more information.
Automation Tab
Automation Settings
Settings related to the automatic processing of files by the connector.
- Send Whether files arriving at the connector are automatically sent as OFTP messages.
- Retry Interval The number of minutes before a failed send is retried. A retry is triggered when the server does not respond to a send attempt, or responds negatively to communicate that the file was not received.
- Max Attempts The maximum number of times the connector processes the input file. Success is based on a successful server acknowledgement and validation of the receipt (when requested synchronously). If you set this to 0, the connector retries the file indefinitely.
- Resend Interval The number of minutes before unacknowledged messages are resent. A resend is triggered when the server receives the file, but an asynchronous MDN receipt is not provided within the expected time frame.
- Max Attempts (async) The maximum number of times the connector processes the input file when asynchronous receipts are requested. Success is based on the return of an asynchronous receipt within the Resend Interval after a successful server acknowledgement. If a successful server acknowledgement is not returned, Max Attempts is applied instead. If this is set to 0, the connector resends the file indefinitely.
- Receive Whether the connector should automatically make pull requests to receive messages from the trading partner.
- Receive Interval The interval between automatic download attempts.
- 毎時何分 時間単位のスケジュールの分オフセット。上記の受信間隔の設定が Hourly に設定されている場合にのみ適用されます。例えば、この値を5 に設定すると、自動的に1:05、2:05、3:05 のようにダウンロードを行います。
- 時 試行が行われる時刻。上記の受信間隔の設定が Daily 、Weekly、または Monthly に設定されている場合にのみ適用されます。
- 曜日/日付 試行が行われる日。上記の受信間隔の設定が Weekly または Monthly に設定されている場合にのみ適用されます。
- 分 ダウンロードを試行するまでの待機時間。上記の受信間隔の設定が Minute に設定されている場合にのみ適用されます。
- Cron 式 いつ試行するかを決定するcron 式を表す5つの欄の文字列。上記の受信間隔の設定が Advanced に設定されている場合にのみ適用されます。
Performance
コネクタへのリソースの割り当てに関する設定。
- 最大ワーカー数 このコネクタでファイルを処理するためにスレッドプールで消費されるワーカースレッドの最大数。設定された場合、これは設定 > オートメーションページのデフォルト設定をオーバーライドします。
- 最大ファイル数 コネクタに割り当てられた各スレッドが送信するファイルの最大数。設定された場合、これは設定 > オートメーションページのデフォルト設定をオーバーライドします。
アラートタブ
アラートとサービスレベル(SLA)の設定に関連する設定。
コネクタのE メール設定
サービスレベル(SLA)を実行する前に、通知用のE メールアラートを設定する必要があります。アラートを設定をクリックすると、新しいブラウザウィンドウで設定ページが開き、システム全体のアラートを設定することができます。詳しくは、アラートを参照してください。
サービスレベル(SLA)の設定
サービスレベルでは、フロー内のコネクタが送受信すると予想される処理量を設定し、その量が満たされると予想される時間枠を設定できます。CData Arc は、サービスレベルが満たされていない場合にユーザーに警告するE メールを送信し、SLA を At Risk(危険) としてマークします。これは、サービスレベルがすぐに満たされない場合に Violated(違反) としてマークされることを意味します。これにより、ユーザーはサービスレベルが満たされていない理由を特定し、適切な措置を講じることができます。At Risk の期間内にサービスレベルが満たされなかった場合、SLA はViolated としてマークされ、ユーザーに再度通知されます。
サービスレベルを定義するには、予想処理量の条件を追加をクリックします。
- コネクタに個別の送信アクションと受信アクションがある場合は、ラジオボタンを使用してSLA に関連する方向を指定します。
- 検知基準(最小)を、処理が予想されるトランザクションの最小値(量)に設定し、毎フィールドを使用して期間を指定します。
- デフォルトでは、SLA は毎日有効です。これを変更するには、毎日のチェックをOFF にし、希望する曜日のチェックをON にします。
- 期間終了前にステータスを’At Risk’ に設定するタイミングを使用して、SLA がAt Risk としてマークされるようにします。
- デフォルトでは、通知はSLA が違反のステータスになるまで送信されません。これを変更するには、‘At Risk’ 通知を送信のチェックをON にします。
次の例は、月曜日から金曜日まで毎日1000ファイルを受信すると予想されるコネクタに対して構成されたSLA を示しています。1000ファイルが受信されていない場合、期間終了の1時間前にAt Risk 通知が送信されます。

Advanced Tab
Optional Certificates (PEM/CER Format)
Settings related to additional certificates to use for enhanced security.
- Auth Challenge Certificate The public key certificate to present when challenged by the server to verify authenticity.
- Verification Certificate The public key certificate to use when verifying digital signatures on incoming messages.
- Receipt Verification Certificate The public key certificate to use when verifying digital signatures on incoming receipts.
- Rollover Certificate An additional certificate to use for authentication. This is useful when you need an overlap period while changing certificates.
- Rollover Verification Certificate An additional certificate to use for signature verification. This is useful when you need an overlap period while changing certificates.
Alternate Local Profile
Settings that override the OFTP configuration on the Profile page. Setting an alternate local profile allows the use of different local certificates and identifiers for certain trading partners.
- SSID Your Odette identifier. This overrides the Odette Identifier on the Profiles tab. When set, the OFTP server uses the alternate SSID and password for this partner. When sending, this ID is used as the file sender and for session authentication, unless it is overridden by the relaying partner. If SSID and SFID are both set, the SFID is used when sending the file.
- Password The local identifier password.
- SFID When accepting incoming OFTP files, CData Arc processes messages in this connector as if they were relayed from the local OFTP profile. Unless this value is set, incoming network connections are greeted with the SSID and password from the OFTP profile. If SSID and SFID are both set, the SFID is used when sending the file.
- Private Certificate The certificate used to decrypt incoming messages and sign outgoing messages. This overrides the Data Decryption Certificate setting on the Profiles page.
- Certificate Password The password required to access the local private certificate.
TLS Client Authentication
Settings related to client authentication when two-way TLS authentication is required.
- Use Profile Settings Use the private certificate on the Profiles page.
- Private Certificate The private certificate presented during TLS client authentication.
- Certificate Password The password required to access the TLS client certificate.
Automatic Certificate Identification
The fields in this section let you specify patterns that allow the connector to automatically identify certificates. The default wildcard character in each field (*) instructs the connector to not search for each pattern.
Proxy Settings
These are a collection of settings that identify and authenticate to the proxy through which the OFTP connection should be routed. By default, this section uses the global settings on the Settings Page. Clear the checkbox to supply settings specific to your OFTP connector.
- プロキシの種類 プロキシベースのファイアウォールで使用されるプロトコル。
- プロキシホスト プロキシベースのファイアウォールの名前またはIP アドレス。
- プロキシポート プロキシベースのファイアウォールのTCP ポート。
- プロキシユーザー プロキシベースのファイアウォールでの認証に使用するユーザー名。
- プロキシパスワード プロキシベースのファイアウォールに認証するために使われるパスワード。
- 認証スキーム デフォルトのNone のままにするか、以下の認証スキームから1つを選択します:Basic、Digest、Proprietary、NTLM。
Advanced Settings
- Credit Count The maximum credit value to be sent in the initial connection (SSID command).
- Encryption Algorithm The algorithm to use when encrypting outgoing messages.
- Exchange Buffer Size The data exchange buffer size, in bytes, to be sent in the initial connection (SSID command).
- Enforce Protocol Version Whether to accept protocol versions not configured for this partner.
- File Description Map The map to set file description text for sending files. Use a semi-colon-delimited list of glob patterns for matching filenames. For example,
INVOICE*=This is an invoice;*ORDER*=This is an order. - Max Record Size When the virtual file format is Fixed or Variable, this field determines the maximum size of each record. The default record size is 128.
- File Hash Algorithm The file hash algorithm to use.
- Receipt Hash Algorithm The receipt hash algorithm to use.
- 処理の遅延 インプットフォルダに置かれたファイルの処理を遅延させる時間(秒)。これは旧式の設定です。代替として、ローカルファイルシステムの管理にはFile コネクタの使用がベストプラクティスです。
- Received Filename Format Incoming files are written to the Output tab using this filename convention. You can use the following macros to ensure that unique filenames are generated:
%VirtualFilename%
%VirtualFileDate%
%GUID% - TLS Enabled Protocols The list of TLS/SSL protocols supported when establishing outgoing connections. Best practice is to only use TLS protocols. Some obsolete operating systems do not support TLS 1.2.
- Virtual Filename Map The map from local filenames to outgoing virtual filenames to use when sending files. Use a semi-colon-delimited list of glob patterns for matching filenames. For example,
INVOICE*=filename1;*ORDER*=filename2.
Message
Message settings determine how the connector searches for messages and manages them after processing. You can save messages to your Sent folder or you can group them based on a Sent folder scheme, as described below.
- Sent フォルダに保存 チェックすると、コネクタで処理されたファイルをコネクタのSent フォルダにコピーします。
- Sent Folder Scheme Instructs the connector to group files in the Sent folder according to the selected interval. For example, the Weekly option instructs the connector to create a new subfolder each week and store all sent files for the week in that folder. The blank setting instructs the connector to save all files directly in the Sent folder. For connectors that process many transactions, using subfolders can help keep files organized and improve performance.
Logging
Settings that govern the creation and storage of logs.
- Log Level The verbosity of logs generated by the connector. When you request support, set this to Debug.
- Log Subfolder Scheme Instructs the connector to group files in the Logs folder according to the selected interval. For example, the Weekly option instructs the connector to create a new subfolder each week and store all logs for the week in that folder. The blank setting tells the connector to save all logs directly in the Logs folder. For connectors that process many transactions, using subfolders helps keep logs organized and improves performance.
- Log Messages Check this to have the log entry for a processed file include a copy of the file itself. If you disable this, you might not be able to download a copy of the file from the Input or Output tabs.
Miscellaneous
Miscellaneous settings are for specific use cases.
- Other Settings Enables you to configure hidden connector settings in a semicolon-separated list (for example,
setting1=value1;setting2=value2). Normal connector use cases and functionality should not require the use of these settings.
Establishing a Connection
The following settings are required to establish an outgoing OFTP connection:
- Identifier (the trading partner’s identifier)
- Password (the password associated with the trading partner’s identifier)
- Remote Host
- Port
After establishing a connection, the appropriate trading partner certificates must be configured before files can be securely transferred.
Send and Receive Files
Once the OFTP profile and partner-specific OFTP connectors have been configured, files can be securely sent and received.
Send Files
In an OFTP connector, the Input tab displays the files to be sent to the target trading partner. If Send Automation is enabled on the Automation tab, files that reach the Input tab of the connector are automatically packaged and sent. Access the log files for all transmissions by expanding the row associated with the transmitted file.
The Create Test Files button lets you generate a simple series of test files to send to the trading partner.
Resend and Retry
An OFTP Resend is triggered when the trading partner is expected to return an asynchronous receipt, but fails to do so within the Resend Interval duration (60 minutes by default). The application then attempts to resend the transmission. The application continues resending the message until a receipt is received or the Max Attempts (async) is exhausted.
A Retry is triggered when the protocol response from the trading partner’s system indicates that the server has not received the transmission. This can indicate a networking or connectivity issue, which is often transient. The application retries the transmission every Retry Interval minutes until the transmission is received or the Max Attempts is exhausted.
Receive Files
In an OFTP connector, the Output tab displays the files that have been received by the application and routed to the connector. Files are routed to a specific OFTP connector based on the Odette identifier present in the incoming OFTP message. Expand each file row to display a list of available logs for the transmission.
These files are available on the connector Output tab. If the connector is connected to other connectors in the flow, files are automatically moved from the Output tab of the OFTP connector to the Input tab of the next connector in the flow.
Message Routing
Each OFTP connector is configured to connect to a single OFTP entity. Sometimes using OFTP requires a routing scenario where a file originating at one OFTP entity (agent A in the image below) needs to pass through another OFTP entity (agent B) to reach the destination OFTP entity (agent C).
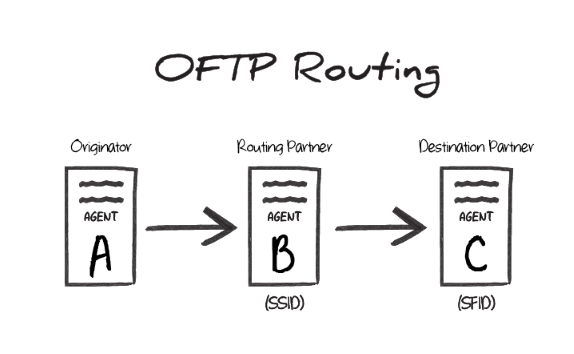
In this scenario, the Odette identifier of agent B is the SSID value during the transfer, and the Odette identifier of agent C is the SFID. In other words, the SSID identifies the ‘middleman’ server that the originator connects to, and the SFID identifies the target entity that this ‘middleman’ should route the OFTP message to.
OFTP Routing in CData Arc
To accomplish this routing scenario in Arc, configure one OFTP connector to connect to agent B (the ‘middleman’ server) and another OFTP connector to connect to agent C (the destination server).
Set the Routing Partner field (in the Routing portion of the Settings tab) for the agent C connector to the OFTP connector that is configured to connect to agent B.
Files to send out to the destination server should be processed by the OFTP connector configured to connect to agent C. The other OFTP connector (targeting agent B) is used behind-the-scenes to route the message, but does not directly process files in the Flow.
SSID vs SFID
If a partner provides a single identifier that they call an SFID, configure an OFTP connector to connect with this entity, and use the SFID as the SSID. If the partner provides an SFID value and an SSID value, the SFID corresponds to server C in the above scenario, and the SSID corresponds to server B.