Email Receive Connector
Version 23.4.8841
Version 23.4.8841
Email Receive Connector
The Email Receive connector supports retrieving messages from an IMAP mail server.
Overview
The Email Receive connector provides a simple way to automate the process of receiving emails. The connector connects to an IMAP server and polls a specified mailbox for new messages to process. By default the connector only receives messages that have not yet been processed, and it supports additional IMAP filters.
The connector supports receiving entire messages in EML format or only downloading attachments on the emails being processed.
Connector Configuration
This section contains all of the configurable connector properties.
Settings Tab
Email Receive Configuration
Settings related to establishing the connection.
- Connector Id The static, unique identifier for the connector.
- Connector Type Displays the connector name and a description of what it does.
- Connector Description An optional field to provide a free-form description of the connector and its role in the flow.
IMAP Connection
Settings related to establishing the connection to the IMAP server.
- Host The hostname or IP address of the IMAP server.
- Port The port on which to connect to the IMAP server. Typical values include 143 and 993.
- Mailbox The IMAP mailbox to poll for messages.
- TLS Type The method used to negotiate SSL/TLS when connecting to the server:
STARTTLS: A plain text connection is established. Afterwards, SSL/TLS can be started with an explicit command.
SSL/TLS: Negotiation occurs immediately without first establishing a plain text connection.
None (Plain Text): A plain text connection is established, and no SSL/TLS is used.
Authentication
Settings related to authenticating the connection.
- User The username to login to the IMAP server.
- Authentication Method Choose between Basic and OAuth 2.0. The options change based on your choice.
- Password (Basic) The password to the IMAP server.
- Auth URL (OAuth 2.0) The authorization URL for the service. This is the URL you are directed to when clicking the Connect button to log in and grant permission to the application.
- Access Token URL (OAuth 2.0) The URL to the access token.
- Client Id (OAuth 2.0) The client Id assigned when you registered for OAuth.
- Client Secret (OAuth 2.0) The secret assigned when you registered for OAuth.
- Scope (OAuth 2.0) A list of scopes that the application should have access to.
- Callback URL (OAuth 2.0) The URL where the service you connect to returns tokens to provide access. Services often require you to whitelist the URLs that are allowed, so this is the value to use when configuring the application registration with your service.
Download
Settings related to processing messages.
- New Messages Whether to only process new messages. This is usually controlled by tracking the UID of downloaded messages. If the UID values become invalid, the connector falls back to using the timestamp of the last processed message or the Days to Search setting if no messages have been processed.
- Days to Search The number of days to search for messages. If Only process new messages is checked, this value is only used if the connector cannot search by UID or the timestamp of the last processed message.
- Additional Search Filters Supply an IMAP RFC compliant search filter to append to the query that is automatically built based on the New Messages and Days to Search settings.
- Download Type Choose to download full messages in EML format or only email attachments.
- Delete Emails Whether to delete successfully downloaded messages from the mailbox.
- Expunge After Delete Whether to permanently remove emails marked for delete. Important: If you choose this option, there is no way to restore expunged emails.
Automation Tab
Automation Settings
Settings related to the automatic processing of files by the connector.
- Receive Whether the connector should automatically poll the remote mailbox for messages to download.
- Receive Interval The interval between automatic download attempts.
- Minutes Past the Hour The minutes offset for an hourly schedule. Only applicable when the interval setting above is set to Hourly. For example, if this value is set to 5, the automation service downloads at 1:05, 2:05, 3:05, etc.
- Time The time of day that the attempt should occur. Only applicable when the interval setting above is set to Daily, Weekly, or Monthly.
- Day The day on which the attempt should occur. Only applicable when the interval setting above is set to Weekly or Monthly.
- Minutes The number of minutes to wait before attempting the download. Only applicable when the interval setting above is set to Minute.
- Cron Expression A five-position string representing a cron expression that determines when the attempt should occur. Only applicable when the interval setting above is set to Advanced.
アラートタブ
アラートとサービスレベル(SLA)の設定に関連する設定.
コネクタのE メール設定
サービスレベル(SLA)を実行する前に、通知用のE メールアラートを設定する必要があります。アラートを設定をクリックすると、新しいブラウザウィンドウで設定ページが開き、システム全体のアラートを設定することができます。詳しくは、アラートを参照してください。
サービスレベル(SLA)の設定
サービスレベルでは、フロー内のコネクタが送受信すると予想される処理量を設定し、その量が満たされると予想される時間枠を設定できます。CData Arc は、サービスレベルが満たされていない場合にユーザーに警告するE メールを送信し、SLA を At Risk(危険) としてマークします。これは、サービスレベルがすぐに満たされない場合に Violated(違反) としてマークされることを意味します。これにより、ユーザーはサービスレベルが満たされていない理由を特定し、適切な措置を講じることができます。At Risk の期間内にサービスレベルが満たされなかった場合、SLA はViolated としてマークされ、ユーザーに再度通知されます。
サービスレベルを定義するには、予想処理量の条件を追加をクリックします。
- コネクタに個別の送信アクションと受信アクションがある場合は、ラジオボタンを使用してSLA に関連する方向を指定します。
- 検知基準(最小)を、処理が予想されるトランザクションの最小値(量)に設定し、毎フィールドを使用して期間を指定します。
- デフォルトでは、SLA は毎日有効です。これを変更するには、毎日のチェックをOFF にし、希望する曜日のチェックをON にします。
- 期間終了前にステータスを’At Risk’ に設定するタイミングを使用して、SLA がAt Risk としてマークされるようにします。
- デフォルトでは、通知はSLA が違反のステータスになるまで送信されません。これを変更するには、‘At Risk’ 通知を送信のチェックをON にします。
次の例は、月曜日から金曜日まで毎日1000ファイルを受信すると予想されるコネクタに対して構成されたSLA を示しています。1000ファイルが受信されていない場合、期間終了の1時間前にAt Risk 通知が送信されます。
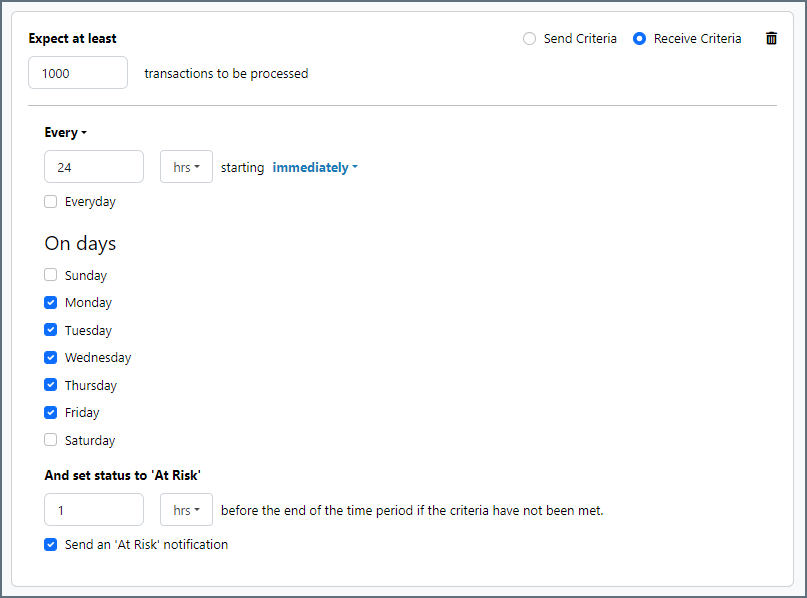
Advanced Tab
Proxy Settings
These are a collection of settings that identify and authenticate to the proxy through which the Email Receive connection should be routed. By default, this section uses the global settings on the Settings Page. Clear the checkbox to supply settings specific to your Email Receive connector.
- Proxy Type The protocol used by a proxy-based firewall.
- Proxy Host The name or IP address of a proxy-based firewall.
- Proxy Port The TCP port for a proxy-based firewall.
- Proxy User The user name to use to authenticate with a proxy-based firewall.
- Proxy Password A password used to authenticate to a proxy-based firewall.
- Authentication Scheme Leave the default None or choose from one of the following authentication schemes: Basic, Digest, Proprietary, or NTLM.
Advanced Settings
Settings not included in the previous categories.
- IMAP Headers A comma-delimited list of headers from the IMAP message that should be promoted as metadata in the downloaded file.
- Incoming Server Public Certificate This field only needs to be set if you are communicating with an IMAPS server. If the IMAP server is an SSL server, set this field to the SSL certificate that identifies the server. If the server’s certificate is not available, you can set this field to Any Certificate to implicitly trust the server’s identity.
Important: If this field is used improperly, it creates a security risk. Use extreme caution when setting this field. - Command Timeout (seconds) The command execution timeout duration in seconds.
- Local File Scheme A scheme for assigning filenames to messages that are output by the connector. You can use macros in your filenames dynamically to include information such as identifiers and timestamps. For more information, see Macros.
Message
Message settings determine how the connector searches for messages and manages them after processing. You can save messages to your Sent folder or you can group them based on a Sent folder scheme, as described below.
- Save to Sent Folder A toggle that instructs the connector to keep a copy of sent messages in the Sent folder.
- Sent Folder Scheme Instructs the connector to group files in the Sent folder according to the selected interval. For example, the Weekly option instructs the connector to create a new subfolder each week and store all sent files for the week in that folder. The blank setting instructs the connector to save all files directly in the Sent folder. For connectors that process many transactions, using subfolders can help keep files organized and improve performance.
Logging
- Log Level The verbosity of logs generated by the connector. When you request support, set this to Debug.
- Log Subfolder Scheme Instructs the connector to group files in the Logs folder according to the selected interval. For example, the Weekly option instructs the connector to create a new subfolder each week and store all logs for the week in that folder. The blank setting tells the connector to save all logs directly in the Logs folder. For connectors that process many transactions, using subfolders helps keep logs organized and improves performance.
- Log Messages Check this to have the log entry for a processed file include a copy of the file itself. If you disable this, you might not be able to download a copy of the file from the Input or Output tabs.
Miscellaneous
Miscellaneous settings are for specific use cases.
- Other Settings Enables you to configure hidden connector settings in a semicolon-separated list (for example,
setting1=value1;setting2=value2). Normal connector use cases and functionality should not require the use of these settings.
Establishing a Connection
The following settings are required to establish a network-level connection to the IMAP server:
- Host
- Port
- TLS Type
Use the Test Connection button to verify that the connector can reach the server.
Once network-level connectivity has been established, the following settings are required to access the messages stored on the IMAP server:
- User
- Password or OAuth 2.0 authentication credentials
- Mailbox
Receiving Emails
If Receive Automation is enabled, the Email Receive connector automatically polls the configured IMAP mailbox for messages to download. By default, the connector only receives messages it has not already downloaded. The first time the connector receives messages, use the Days to Search setting in the Download configuration section to specify the range of messages to download.
Messages can also be manually retrieved by clicking the Receive button on the Output tab of the connector.
The Download Type setting determines whether full messages or just message attachments are downloaded. Downloaded files are placed in the Output Folder or passed along to the next connector in the flow.
Search Filters
The IMAP Search Filter setting allows for further customization of the range of messages to retrieve. This field accepts standard IMAP protocol filters and only downloads messages that match the configured filters.
The following filters are supported:
| <message set> | Messages with message sequence numbers corresponding to the specified message sequence number set. |
| ALL | All messages in the mailbox: this is the default initial key for AND-ing. |
| ANSWERED | Messages with the \Answered flag set. |
| BCC <string> | Messages that contain the specified string in the envelope structure's BCC field. |
| BEFORE <date> | Messages whose internal date is earlier than the specified date. |
| BODY <string> | Messages that contain the specified string in the body of the message. |
| CC <string> | Messages that contain the specified string in the envelope structure's CC field. |
| DELETED | Messages with the \Deleted flag set. |
| DRAFT | Messages with the \Draft flag set. |
| FLAGGED | Messages with the \Flagged flag set. |
| FROM <string> | Messages that contain the specified string in the envelope structure's FROM field. |
| HEADER <field-name> <string> | Messages that have a header with the specified field-name (as defined in [RFC-822]) and that contain the specified string in the [RFC-822] field-body. |
| KEYWORD <flag> | Messages with the specified keyword set. |
| LARGER <n> | Messages with an RFC822.SIZE larger than the specified number of octets. |
| NEW | Messages that have the \Recent flag set but not the \Seen flag. This is functionally equivalent to "(RECENT UNSEEN)". |
| NOT <search-key> | Messages that do not match the specified search key. |
| OLD | Messages that do not have the \Recent flag set. This is functionally equivalent to "NOT RECENT" (as opposed to "NOT NEW"). |
| ON <date> | Messages whose internal date is within the specified date. |
| OR <search-key1> <search-key2> | Messages that match either search key. |
| RECENT | Messages that have the \Recent flag set. |
| SEEN | Messages that have the \Seen flag set. |
| SENTBEFORE <date> | Messages whose [RFC-822] Date: header is earlier than the specified date. |
| SENTON <date> | Messages whose [RFC-822] Date: header is within the specified date. |
| SENTSINCE <date> | Messages whose [RFC-822] Date: header is within or later than the specified date. |
| SINCE <date> | Messages whose internal date is within or later than the specified date. |
| SMALLER <n> | Messages with an RFC822.SIZE smaller than the specified number of octets. |
| SUBJECT <string> | Messages that contain the specified string in the envelope structure's SUBJECT field. |
| TEXT <string> | Messages that contain the specified string in the header or body of the message. |
| TO <string> | Messages that contain the specified string in the envelope structure's TO field. |
| UID <message set> | Messages with unique identifiers corresponding to the specified unique identifier set. |
| UNANSWERED | Messages that do not have the \Answered flag set. |
| UNDELETED | Messages that do not have the \Deleted flag set. |
| UNDRAFT | Messages that do not have the \Draft flag set. |
| UNFLAGGED | Messages that do not have the \Flagged flag set. |
| UNKEYWORD <flag> | Messages that do not have the specified keyword set. |
| UNSEEN | Messages that do not have the \Seen flag set. |
Macros
Using macros in file naming strategies can enhance organizational efficiency and contextual understanding of data. By incorporating macros into filenames, you can dynamically include relevant information such as identifiers, timestamps, and header information, providing valuable context to each file. This helps ensure that filenames reflect details important to your organization.
CData Arc supports these macros, which all use the following syntax: %Macro%.
| Macro | Description |
|---|---|
| ConnectorID | Evaluates to the ConnectorID of the connector. |
| Ext | Evaluates to the file extension of the file currently being processed by the connector. |
| Filename | Evaluates to the filename (extension included) of the file currently being processed by the connector. |
| FilenameNoExt | Evaluates to the filename (without the extension) of the file currently being processed by the connector. |
| MessageId | Evaluates to the MessageId of the message being output by the connector. |
| RegexFilename:pattern | Applies a RegEx pattern to the filename of the file currently being processed by the connector. |
| Header:headername | Evaluates to the value of a targeted header (headername) on the current message being processed by the connector. |
| LongDate | Evaluates to the current datetime of the system in long-handed format (for example, Wednesday, January 24, 2024). |
| ShortDate | Evaluates to the current datetime of the system in a yyyy-MM-dd format (for example, 2024-01-24). |
| DateFormat:format | Evaluates to the current datetime of the system in the specified format (format). See サンプル日付フォーマット for the available datetime formats |
| Vault:vaultitem | Evaluates to the value of the specified vault item. |
| Subject | Evaluates to the subject of the email currently being received by the connector. |
Examples
Some macros, such as %Ext% and %ShortDate%, do not require an argument, but others do. All macros that take an argument use the following syntax: %Macro:argument%
Here are some examples of the macros that take an argument:
- %Header:headername%: Where
headernameis the name of a header on a message. - %Header:mycustomheader% resolves to the value of the
mycustomheaderheader set on the input message. - %Header:ponum% resolves to the value of the
ponumheader set on the input message. - %RegexFilename:pattern%: Where
patternis a regex pattern. For example,%RegexFilename:^([\w][A-Za-z]+)%matches and resolves to the first word in the filename and is case insensitive (test_file.xmlresolves totest). - %Vault:vaultitem%: Where
vaultitemis the name of an item in the vault. For example,%Vault:companyname%resolves to the value of thecompanynameitem stored in the vault. - %DateFormat:format%: Where
formatis an accepted date format (see サンプル日付フォーマット for details). For example,%DateFormat:yyyy-MM-dd-HH-mm-ss-fff%resolves to the date and timestamp on the file.
You can also create more sophisticated macros, as shown in the following examples:
- Combining multiple macros in one filename:
%DateFormat:yyyy-MM-dd-HH-mm-ss-fff%%EXT% - Including text outside of the macro:
MyFile_%DateFormat:yyyy-MM-dd-HH-mm-ss-fff% - Including text within the macro:
%DateFormat:'DateProcessed-'yyyy-MM-dd_'TimeProcessed-'HH-mm-ss%